Mongo-TLS Implementation
Hey, Glad you are here, I hope you are doing great. Without any further delay lets get started with my first ever article over here. So all I have here is some stuff regarding how we implement Mongo-TLS connection using java-spring boot. This was my first ever piece of code in my job. At my workplace we did this because recently our database have been moved to document db that was offered by amazon.
Tools :
- Any Java IDE of your choice
- Mongo SSL Instance (mongodb-ssl-4.0.23)
Create Trusted Keystore File:
- Download the pem file from the path wget s3.amazonaws.com/rds-downloads/rds-combined..
- After downloading, generate a keystore by using keytool which can be used by Java app command to generate keystore : docs.oracle.com/cd/E19798-01/821-1841/gjrgy or go over here for detailed explanation : %[stackoverflow.com/questions/3997748/how-can..
- Once you have them ready, It is recommended to have them in same folder.
Lets take a look at the dependencies we need:
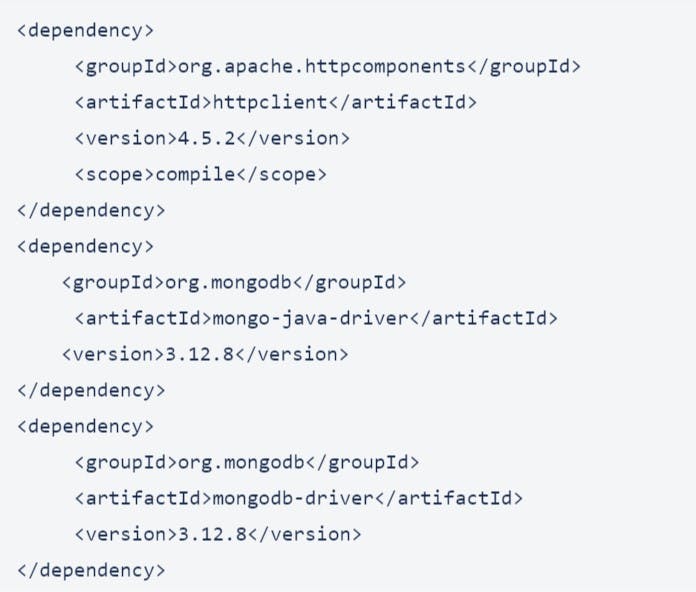
You are good to go once you have them.
Implementation using java:
I assume you're using Java 8 and Spring version can be >=1.5, Lets take a look how easy it is to make our service use tls connection.
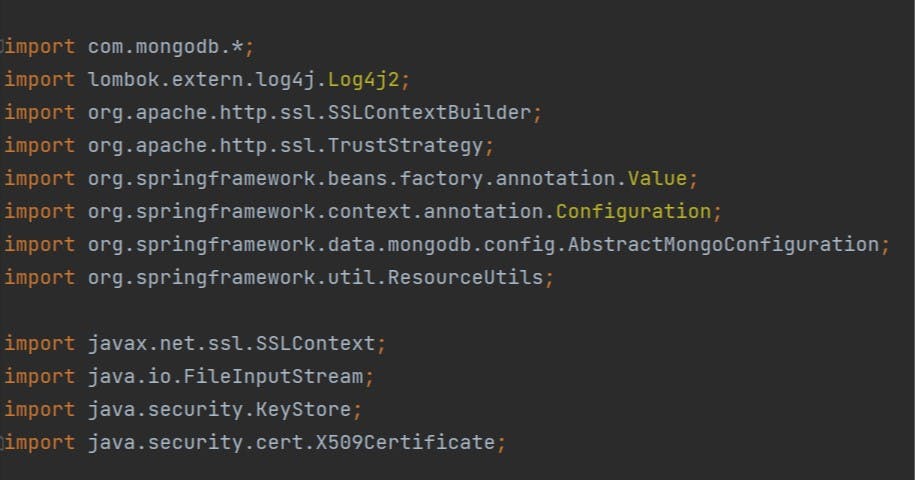
Lets take a look at what all the imports we needed.
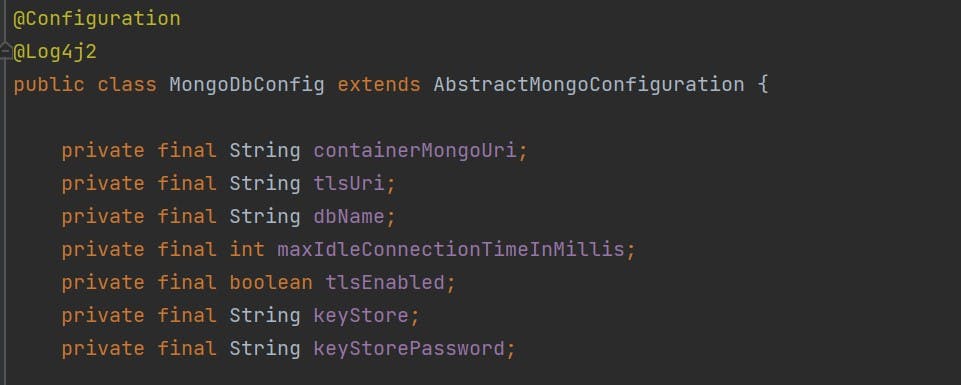
Lets create a class called MongoDbConfig and extend the AbstractMongoConfiguration. Its have to nice clean and readable named variables.
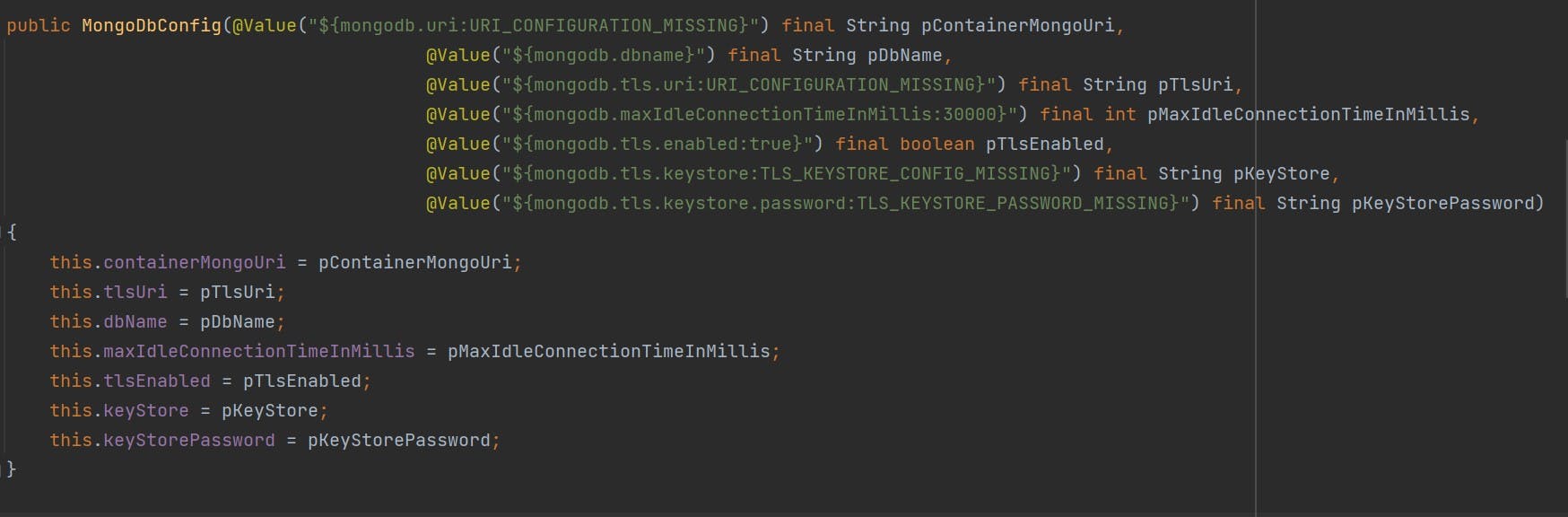
Now its time to inject the values from application.properties or yaml file, its your choice Its a nice practice to have your constructor parameters prefixed with 'p'
Alright, as we extend the AbstractMongoConfiguration, it will ask you to override few methods such as getDatabaseName, Mongo instance method.
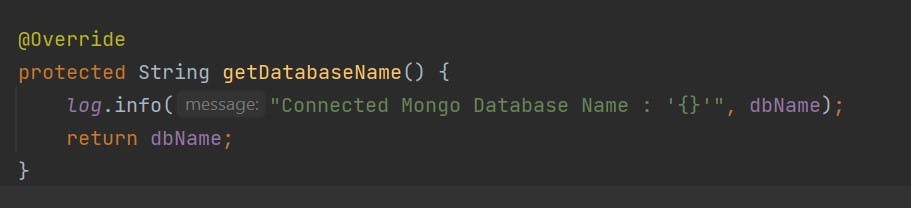
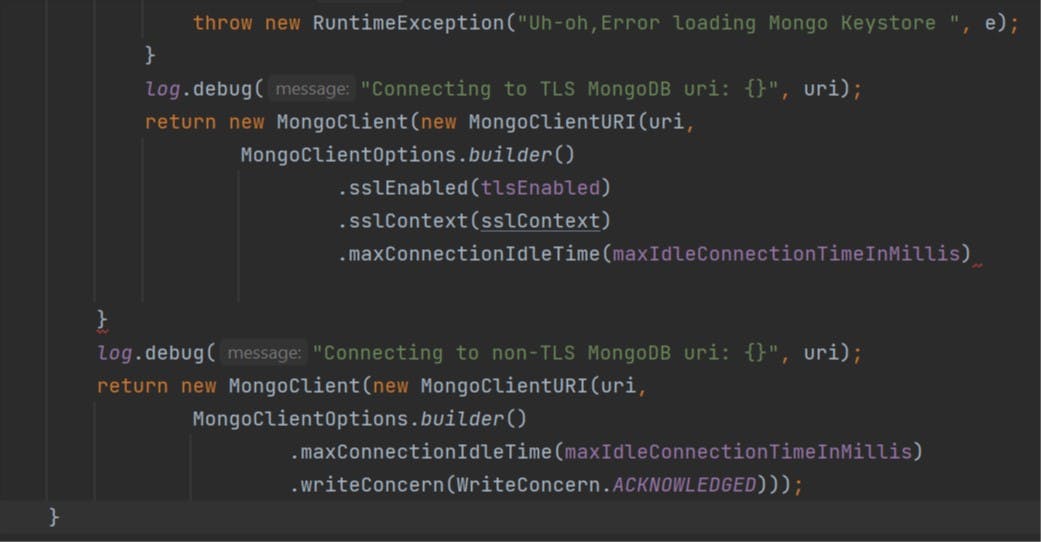
Now coming to main part of our code where all the magic happens in few lines of code
So what we doing over here?
Its pretty straight-forward as you see, no complex stuff. You get the TLS uri if TLS is enabled and goes into if part, and we have character array that stores the password of our keystore we have a Trust Strategy in here, its nothing but A strategy to establish trustworthiness of certificates without consulting the trust manager configured in the actual SSL context. The next part is SSL context that basically holds the what is the protocol we used, provider, context-spi stuff, you can check out them if you debug it.
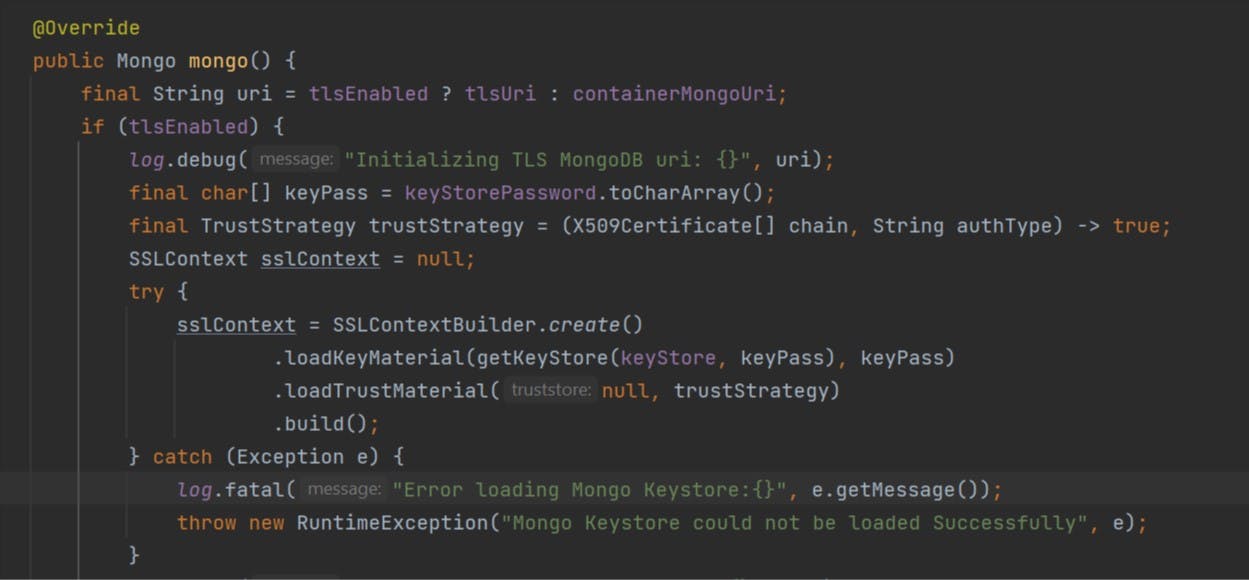
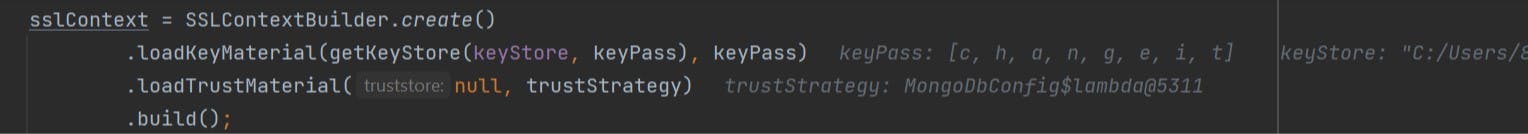
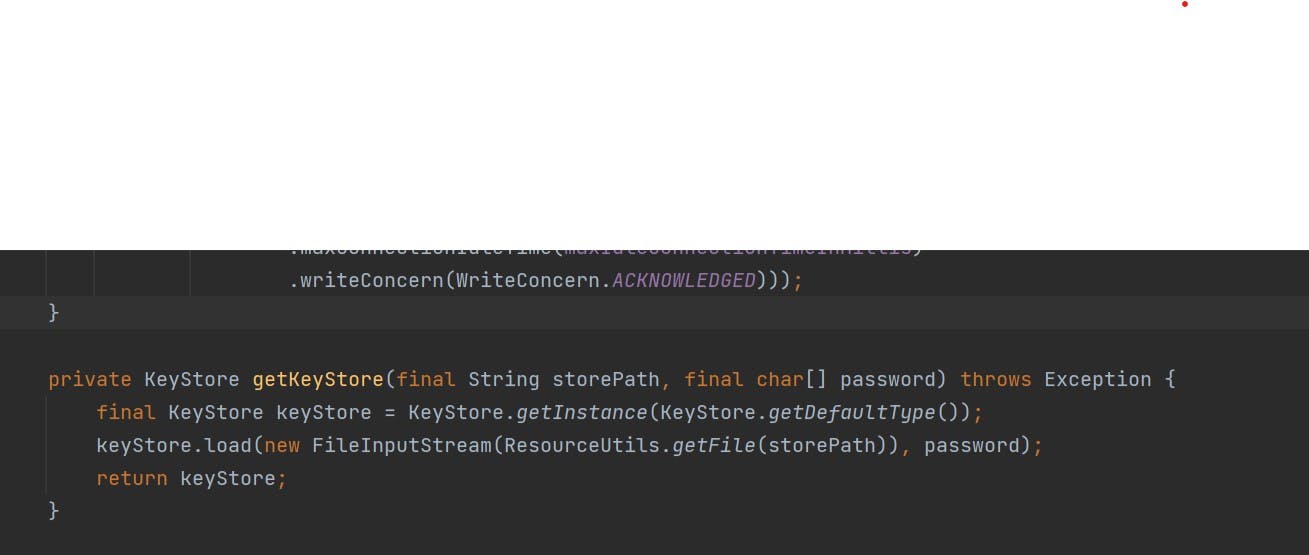
The try block we have does all the job, it gets the keypass and keystore by calling loadKeyMaterial and gets the truststrategy by loadTrustMaterial. Below is the referenced pic of how it looks if we debug
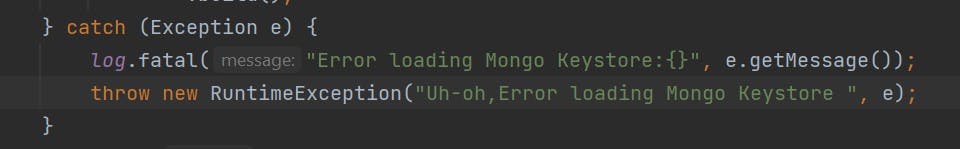
The catch block exits from the application if it fails to load keystore, no point if we continue
Now the final part, once all the verifying has been done, we reach over here
Application.yml :
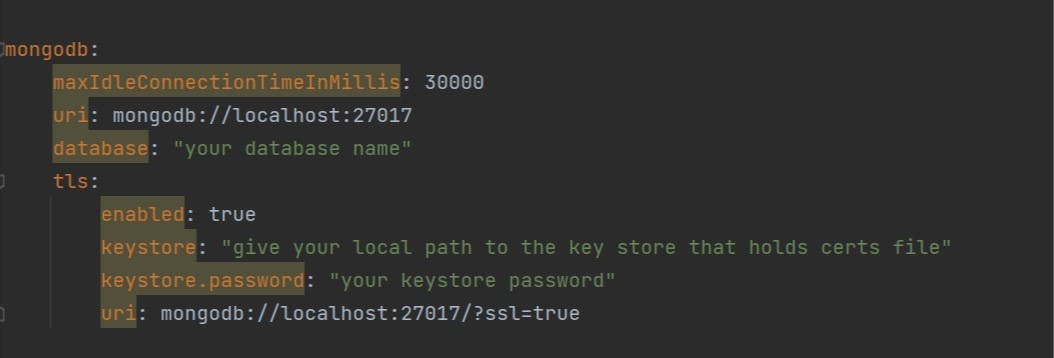
Once you reach here, start your mongo instance from cmd by going into bin directory and hit this command : mongod --sslMode allowSSL --sslPEMKeyFile "your path to pem file" It will wait for connections and later goto your spring app and start the application and once its start running you can see connections getting recieved in your cmd.
That's it, you have successfully implemented tls connection in your service, cheers! Thankyou :)